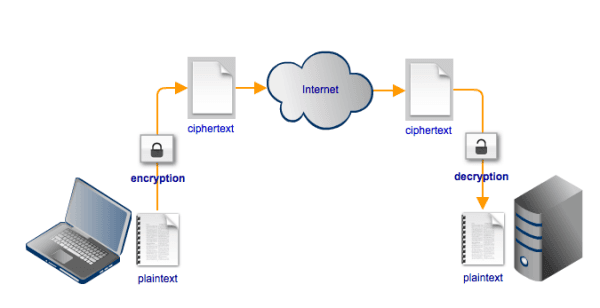
Graphical User Interface (GUI) OptionYou do not need to be an expert to use AES Crypt for Windows to securelyencrypt your data files. To encrypt a file, you simply right-click onthe file you wish to encrypt, select the 'AES Encrypt' option, and enterthe desired password. AES Crypt will produce a file that cannot be readby anybody who does not know the secret password. It is as simple asthat. AES Crypt will produce an encrypted file with the same name as theoriginal file, but with an '.aes' extension. Note that when you encrypt a file with AES Crypt, it does not delete theoriginal file. Generally, people encrypt files for the purpose ofsending a file securely via e-mail or copying it to a portable storagedevice that is more susceptible to loss. As such, most people do not wantto delete the original. However, you may certainly delete the originalfile: just do not forget the password. It is impossible to recover thecontents of an encrypted file if the password is lost. Decrypting an encrypted file produced through the process described above isjust as easy. To decrypt the file, you simply right-click on the encryptedfile, select the 'AES Decrypt' option, and enter your secret password. Command-Line OptionThere is also a command-line (console) application available for Windowsincluded in the installation package and also downloadable as a separateapplication. To encrypt a file, you simply enter the 'aescrypt' command with theapprorpiate command-line arguments. Suppose you have a file called 'picture.jpg' that you would like toencrypt using the password 'apples'. You would enter the followingcommand: That's it! The program will create a file with the name 'picture.jpg.aes'. When you want to later decrypt the file 'picture.jpg.aes', you wouldenter the following command: The program will create the file 'picture.jpg', containing the contents of theoriginal file before it was encrypted. It can't be any simpler than that! In all of the examples above, the password is provided on the commandline. Since there are certain risks associated with that kind of usage,it may be preferred to let aescrypt prompt you to enter the password.This can be accomplished simply by not including the -p parameter,like this: AES Crypt will prompt you for the password, but what you enter will not bedisplayed on the screen. What if you want to decrypt a file, but just want to have it displayed onthe screen and not stored in a plaintext file? That's possible. To dothat, just use this syntax: |

Aes Encryption Software
Aes Encrypt File

Aes Encryption Software
Aes Encrypt File
- The answer: No, the AES key cannot be recovered in this scenario. AES is secure against known-plaintext attack. This means that, even if an attacker knows the plaintext and its corresponding ciphertext (its encryption under some unknown AES key), then the attacker cannot recover the AES key.
- The Advanced Encryption Standard (AES, Rijndael) is a block cipher encryption and decryption algorithm, the most used encryption algorithm in the worldwide. The AES processes block of 128 bits using a secret key of 128, 192, or 256 bits. This article shows you a few of Java AES encryption and decryption examples.
- AES files are useful for protecting sensitive personal and business documents. AES Crypt users often encrypt documents and send them via email. When AES Crypt creates an encrypted file, it append the '.aes' extension to the filename. For example, when AES Crypt encrypts a document named mydocument.docx, it creates a new file named mydocument.
- The output file is generated by including the encrypted AES key at the beginning of the file, followed by the initialization vector (IV) and finally the file data encrypted by AES. This way, just the output file can be delivered to the receiver, instead of the three separate components.
Python File Aes Encryption
The Encrypting File System (EFS) on Microsoft Windows is a feature introduced in version 3.0 of NTFS that provides filesystem-level encryption.The technology enables files to be transparently encrypted to protect confidential data from attackers with physical access to the computer.
